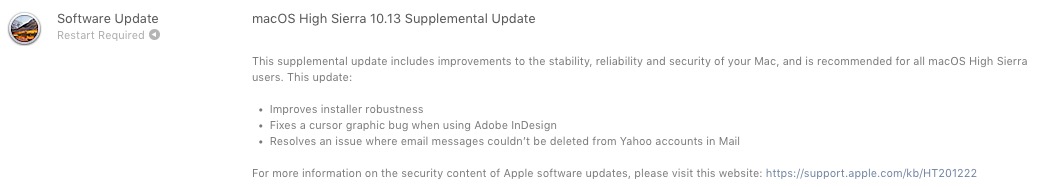
Apple has recently published a very important Supplemental Update for all Mac users who have installed macOS High Sierra 10.13.
In macOS High Sierra 10.13 Supplemental Update are solving some graphic malfunctions for Adobe InDesign and a bugs which did not allow Delete Messages Received In Yahoo Mail Application.
The most serious part of this additional update is related to two security issues, which came "bundled" with the new High Sierra operating system.
Password encryption vulnerability for APFS (Encrypted) - Disk Utility Bug
A bug in the application disk Utility which does visible password for formatted disc volumes APFS Encrypted.
In short, when we enter the encrypted password for a volume, it is required twice, to make sure we didn't type it wrong the first time. Then we have to choose a “hint”(A word or phrase) as a clue to the password. The bug in disk Utility, makes the password visible instead of the word or phrase from "hint". In this way, it is exposed to anyone who has access to the Mac.
The video posted on Twitter shows exactly how to find the APFS encrypted volume password using Disk Utility.
It would be interesting why Apple recommends erasing when diskutil can clear hints:
diskfiled apfs setPassphraseHint [diskXsX] -user disk -clear pic.twitter.com/0khrm8aTq9- Felix Schwarz (@felix_schwarz) October 5, 2017
Vulnerability Keychain Access - bypass user password
Normally and compulsively when we go an account and a password saved in Keychain, is required Mac user password. Through a vulnerability a macOS High Sierra, a bad-intentioned application can extract passwords saved in Keychain Access, skipping the user password Mac by means of a synthetic click. Fake / simulated.
Released October 5, 2017
StorageKit
Available for: macOS High Sierra 10.13
Impact: A local attacker may gain access to an encrypted APFS volume
Description: If a hint was set in Disk Utility when creating an encrypted volume APFS, the password was stored as the hint. This was addressed by clearing hint storage if the hint was the password, and by improving the logic for storing hints.
CVE-2017-7149: Matheus Mariano of Leet Tech
Security
Available for: macOS High Sierra 10.13
Impact: A malicious application can extract keychain passwords
Description: A method exists for applications to bypass the keychain access prompt with a synthetic click. This was addressed by requiring the user password when prompted for keychain access.
CVE-2017-7150: Patrick Wardle of Synack
New downloads of macOS High Sierra 10.13 includes the security content of the macOS High Sierra 10.13 Supplemental Update.
So, if you have macOS High Sierra 10.13, it is highly recommended to do the additional update. It is available via Mac App Store, in the tab "Updates"(And will not change the version number). Apple has already published macOS High Sierra 10.13.1 for developers who have devices in Apple Beta Software Program.







0 thoughts on "Security problems APFS Encrypted and Keychain Access, solved with macOS High Sierra 10.13 Supplemental Update"