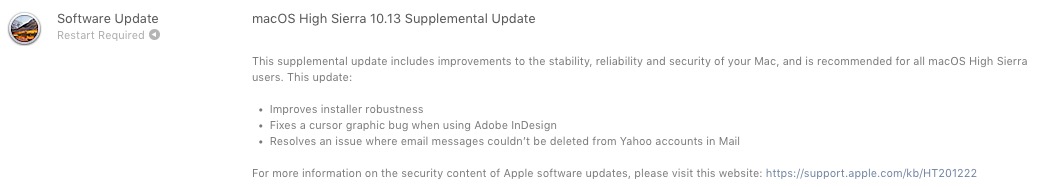
Η Apple δημοσίευσε πρόσφατα μια πολύ σημαντική συμπληρωματική ενημέρωση για όλους τους χρήστες Mac που έχουν εγκαταστήσει macOS High Sierra 10.13.
Σε MacOS High Sierra 10.13 Συμπληρωματική ενημέρωση επίλυση ορισμένων δυσλειτουργίες για το Adobe InDesign και ένα bug που δεν επέτρεπε διαγραφή μηνυμάτων που λαμβάνονται στην εφαρμογή Mail από το Yahoo!.
Το πιο σοβαρό μέρος της αυτή η πρόσθετη ενημέρωση σχετίζεται με δύο ζητήματα ασφαλείας, που ήρθε «ως πακέτο» με το νέο λειτουργικό σύστημα High Sierra.
Ευπάθεια κωδικού πρόσβασης κρυπτογράφησης για APFS (Κρυπτογραφημένο) – Σφάλμα βοηθητικού προγράμματος δίσκου
Ένα bug στην εφαρμογή Βοηθητικό πρόγραμμα δίσκου που κάνει ορατό τον κωδικό πρόσβασης για τόμων δίσκου μορφοποιημένη APFS κρυπτογραφημένα.
Εν ολίγοις, όταν εισάγουμε τον κωδικό κρυπτογράφησης για έναν τόμο, ζητείται δύο φορές, για να είμαστε σίγουροι ότι δεν τον πληκτρολογήσαμε λάθος την πρώτη φορά. Τότε πρέπει να επιλέξουμε ένα "υπόδειξη" (μια λέξη ή φράση) ως υπόδειξη κωδικού πρόσβασης. Το σφάλμα Βοηθητικό πρόγραμμα δίσκου, κάνει τον κωδικό πρόσβασης ορατό αντί για τη λέξη ή τη φράση από το "hint". Με αυτόν τον τρόπο, εκτίθεται σε οποιονδήποτε έχει πρόσβαση στο Mac.
Στο βίντεο που δημοσιεύτηκε στο Twitter, μπορείτε να δείτε ακριβώς πώς μπορείτε να βρείτε τον κωδικό πρόσβασης ενός κρυπτογραφημένου τόμου APFS, χρησιμοποιώντας το Disk Utility.
Θα ήταν ενδιαφέρον γιατί η Apple συνιστά τη διαγραφή όταν το diskutil μπορεί να καθαρίσει υποδείξεις:
diskutil apfs setPassphraseHint [diskXsX] -user disk -clear pic.Twitter.com/0khrm8aTq9— Felix Schwarz (@felix_schwarz) 5 Οκτωβρίου 2017
Ευάλωτη πρόσβαση στην αλυσίδα κλειδιών – παράκαμψη κωδικού πρόσβασης χρήστη
Κανονικά και αναγκαστικά, όταν έχουμε πρόσβαση λογαριασμού και έναν κωδικό πρόσβασης που αποθηκεύονται σε μπρελόκ, ερωτούμαστε κωδικό πρόσβασης του χρήστη Mac. Μέσα από μια ευπάθεια α MacOS υψηλής Sierra, μια κακόβουλη εφαρμογή μπορεί ανάκτηση αποθηκευμένων κωδικών πρόσβασης στο Keychain Access, παρακάμπτοντας τον κωδικό πρόσβασης χρήστη Mac μέσω ενός συνθετικού κλικ. Ψεύτικο / προσομοιωμένο.
Κυκλοφόρησε στις 5 Οκτωβρίου 2017
StorageKit
Διαθέσιμο για: macOS High Sierra 10.13
Αποτέλεσμα: Ένας τοπικός εισβολέας μπορεί να αποκτήσει πρόσβαση σε έναν κρυπτογραφημένο τόμο APFS
Περιγραφή: Εάν είχε οριστεί μια υπόδειξη στο Disk Utility κατά τη δημιουργία ενός κρυπτογραφημένου τόμου APFS, ο κωδικός πρόσβασης αποθηκεύτηκε ως υπόδειξη. Αυτό αντιμετωπίστηκε με την εκκαθάριση του χώρου αποθήκευσης υποδείξεων εάν η υπόδειξη ήταν ο κωδικός πρόσβασης και με τη βελτίωση της λογικής για την αποθήκευση υποδείξεων.
CVE-2017-7149: Matheus Mariano του Leet Tech
Ασφάλεια
Διαθέσιμο για: macOS High Sierra 10.13
Αποτέλεσμα: Μια κακόβουλη εφαρμογή μπορεί να εξάγει κωδικούς πρόσβασης κλειδιών
Περιγραφή: Υπήρχε μια μέθοδος για τις εφαρμογές να παρακάμπτουν την προτροπή πρόσβασης στην αλυσίδα κλειδιού με ένα συνθετικό κλικ. Αυτό αντιμετωπίστηκε με την απαίτηση του κωδικού πρόσβασης χρήστη όταν ζητήθηκε πρόσβαση με μπρελόκ.
CVE-2017-7150: Patrick Wardle του Synack
Οι νέες λήψεις του macOS High Sierra 10.13 περιλαμβάνουν το περιεχόμενο ασφαλείας της συμπληρωματικής ενημέρωσης macOS High Sierra 10.13.
Επομένως, εάν έχετε macOS High Sierra 10.13, συνιστάται ιδιαίτερα να κάνετε την πρόσθετη ενημέρωση. Διατίθεται μέσω Mac App Store, στο tab-ul "Ενημερώσεις"(και δεν θα αλλάξει τον αριθμό έκδοσης). Η Apple έχει ήδη δημοσιεύσει macOS High Sierra 10.13.1 για προγραμματιστές που διαθέτουν συσκευές στο Πρόγραμμα λογισμικού Apple Beta.






1 Σκέφτηκα "Ζητήματα ασφαλείας κρυπτογραφημένα και πρόσβαση στο μπρελόκ, επιλύθηκε με MacOS High Sierra 10.13 Συμπληρωματική ενημέρωση«